Gathering Resources
 By Cynthia Hetherington
By Cynthia Hetherington
Due diligence investigations examine the backgrounds of corporate entities and the principals who manage them. They are applicable to all professionals involved in investigations, insurance and risk managers, attorneys, investigative reporters, security practitioners, and every-day consumers. Business intelligence, open source research (OSINT), and social media research (SOCMINT) are key tools that assist in researching and conducting due diligence.
Hg conducts online backgrounds on businesses, persons, and entities—foreign and domestic. In employing OSINT and SOCMINT skills, we are able to expose fraudulent business enterprises, locate assets, and gather undercover intelligence. In this 4-part series, we discuss how to use public record resources, social media resources and open source monitoring, the difference between fee and free resources, and offer two case studies. This week we tackle critical definitions and share a useful list of documents to consider obtaining for your investigation.
Definitions
Knowing the difference between public records and public information will help you understand some of the differences between online sites and how they gather their data.
Public Records
Public records are records of incidents or actions filed or recorded with a government agency for the purpose of notifying others—the public—about the matter. Deeds are recorded in order to keep track of property owners. Mortgages are recorded to indicate liens on the property. Prospective buyers and lenders search these records to verify ownership and determine if the property is subject to liens or easements. These records are public; anyone requiring details about your property may review or copy these documents.
Public Information
Public information is data that you freely provide to facilitate the flow of commercial and private communications. In today’s tech era, a person’s information becomes public more often than one is even aware. It’s not just your landline number in a phonebook anymore. Information placed on social network sites such as Facebook or LinkedIn becomes public. And when you sign up for a discount card at the local grocery store, you have made information about yourself publicly available to entities purchasing marketing lists.
Investigator’s Approach
Resources gathered during the investigative process are a combination of public records and public information. Combined, they can be social media accounts, statements, recordings, documents, witness interviews, news and media articles, and other published materials.
Documents can also include:
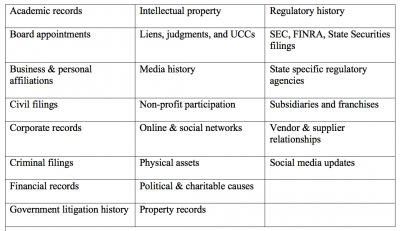
Once you identify the documents you need to begin to fill out your analysis, you need to determine where you will access this information. Next week, we launch into public record resources.

Are you an analyst or investigator looking for advanced OSINT/SOCMINT training on due diligence? If so, check out Hg’s webinar series, where you can attend live sessions and receive CEUs or watch previously recorded sessions to beef up your investigative skills.

Are you interested in working with a company but unsure if it’s legitimate? As veteran investigators in due diligence, Hg understands the business world and the legal and regulatory frameworks in which corporations and privately held companies operate. Our skilled analysts excel at exposing financial risks, reputational issues, criminal activity, and legal actions detrimental to your personal and business stability. Learn how our team can arm you with the data you need.
 Cynthia Hetherington, MLS, MSM, CFE, CII is the founder and president of Hetherington Group, a consulting, publishing, and training firm that leads in due diligence, corporate intelligence, and cyber investigations by keeping pace with the latest security threats and assessments. She has authored three books on how to conduct investigations, is the publisher of the newsletter, Data2know: Internet and Online Intelligence, and annually trains thousands of investigators, security professionals, attorneys, accountants, auditors, military intelligence professionals, and federal, state, and local agencies on best practices in the public and private sectors.
Cynthia Hetherington, MLS, MSM, CFE, CII is the founder and president of Hetherington Group, a consulting, publishing, and training firm that leads in due diligence, corporate intelligence, and cyber investigations by keeping pace with the latest security threats and assessments. She has authored three books on how to conduct investigations, is the publisher of the newsletter, Data2know: Internet and Online Intelligence, and annually trains thousands of investigators, security professionals, attorneys, accountants, auditors, military intelligence professionals, and federal, state, and local agencies on best practices in the public and private sectors.



