By Mariel Klosterman
Junior at Beacom College of Computer and Cyber Sciences, Dakota State University
When you search “sock puppet accounts” using Google, there are a few definitions that show in the search results, and they all follow a common theme. The most common definition is found on Wikipedia’s entry: A sock puppet or sockpuppet is an online identity used for purposes of deception. Daniel Kats, Senior Principal Researcher for NortonLifeLock Research, held a similar view in his article, “Identifying Sockpuppet Accounts on Social Media Platforms:” “We define a sockpuppet as a fictitious online identity created for the purposes of deception.”
Sock puppet accounts are mainly known to those outside the information security field as accounts used for disinformation purposes, such as swaying your opinion about a topic or a product. However, this is not the only way to use a sock puppet account.
For the purposes of this discussion, the following definitions will be used:
- Sock puppet account: An account created for a disingenuous purpose (that is, for a purpose other than what it is meant to be used for). More commonly known as a fake account or alternate account.
- Puppeteer: A person who creates sock puppet accounts for either benign or malicious purposes.
- Malicious actor: A person who, through any means, threatens or attempts to threaten the security of an individual or company for malicious purposes.
In this 4-part blog series, up-and-coming cybersecurity researcher Dakota State University Junior, Mariel Klosterman, describes the how sock puppets are used by malicious actors and OSINT investigators, types of sock puppet accounts, and how to create a sock puppet for information collection. This week she explores how sock puppets can be used to create Personas and Avatars.
Sock Puppet Creations
There are generally two approaches for creating a sock puppet: Persona and Avatar.
Creating a Persona:
A persona is a fake person. For this, you have to come up with names, addresses, jobs, and details that a real person would have. If you are creating a persona, consider creating a female persona. Female sock puppet accounts are more likely to be trusted and come under less suspicion than male accounts.
- Fake Name Generator is one of the generators that generates the most information for a fake person. fakenamegenerator.com
- This Person Does Not Exist generates fake pictures of people. thispersondoesnotexist.com
- This Resume Does Not Exist generates fake resumes for fake people. thisresumedoesnotexist.com
Creating an Avatar:
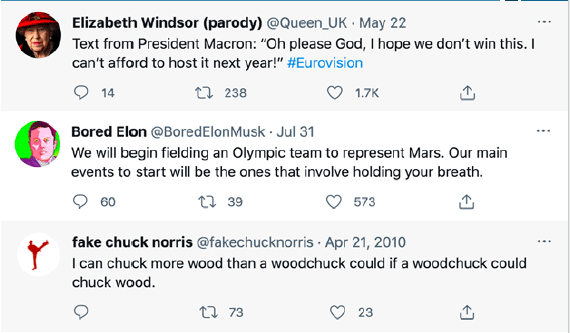
An avatar is usually based around an idea. Unlike a persona, you do not have to create an entire identity, because you are not pretending to be a different person, whether real or imagined. This is a type of account that people understand are not real people, for example, parody accounts.
Parody Accounts (with a screenshot of a recent post)
@Queen_UK
@BoredElonMusk
@FakeChuckNorris
Most OSINT researchers tend to use sock puppets or, more accurately, throwaway accounts for passive reconnaissance. There are a few who combine passive reconnaissance (OSINT) and active reconnaissance (HUMINT) by using a sock puppet to interact with the target of their investigation.
Before creating a sock puppet account, determine the purpose of the account. If you’re going for passive reconnaissance, a throwaway account may be more useful. If you’re going for active reconnaissance, a sock puppet account will likely be more useful.
Sock Puppet Requirements
These items are used to better ensure your privacy and make it more difficult for organizations, other sock puppeteers, or sock puppet hunters to connect your sock puppet to you. You can always choose to remove these items or add others.
- A separate, dedicated computer
- A set of virtual machines (VMs)
- A virtual private network (VPN)
- A separate email address for your sock puppet account
- A profile picture
- A separate “burner” phone
- A blog
Like what you’re reading? Download the entire Hg Summer Factsheet, 21st Century Sock Puppets: Pulling the Wool Over on You, for free today!
 Mariel Klosterman, a junior at Dakota State University, is currently majoring in Network and Security Administration. Her areas of interest are defensive security and open-source intelligence (OSINT). Ms. Klosterman has conducted significant research relating to sock puppet accounts, which are an integral part of OSINT and digital investigations. She has organizational experience writing security policies, conducting security assessments, and implementing data protection controls and training. She is an accomplished speaker, presenting on a wide range of topics in the cyber arena to local professional groups including InfraGard South Dakota. Ms. Klosterman is passionate about security and enjoys sharing her knowledge and skills working for CybHER. Check out her latest projects at www.linkedin.com/in/marielklosterman.
Mariel Klosterman, a junior at Dakota State University, is currently majoring in Network and Security Administration. Her areas of interest are defensive security and open-source intelligence (OSINT). Ms. Klosterman has conducted significant research relating to sock puppet accounts, which are an integral part of OSINT and digital investigations. She has organizational experience writing security policies, conducting security assessments, and implementing data protection controls and training. She is an accomplished speaker, presenting on a wide range of topics in the cyber arena to local professional groups including InfraGard South Dakota. Ms. Klosterman is passionate about security and enjoys sharing her knowledge and skills working for CybHER. Check out her latest projects at www.linkedin.com/in/marielklosterman.




