By Trevor Morgan
Designed for short video clips of content, TikTok is a new form of social media consumption that has taken the world by storm. This quickly growing China-based app has been at the forefront of smart-phone entertainment as of late, specifically during quarantine. If you’re a regular Hg follower on social media, you’re in the know about our love of dogs. If ever you are in need of a good laugh and a warm sense of calm, might we suggest scrolling through TikTok’s For You page where you could stumble upon such adorable pups like this:
In all seriousness, however, after reviewing the content some users post, thoroughly examining TikTok’s privacy policy, and understanding its international implications, some laughing may fall to the wayside. From an open source intelligence perspective, this novelty app provides researchers and investigators with a plethora of knowledge and useful information. On the user end, it might not be all fun and games.
In this new blog series, Hg’s investigative analyst Trevor Morgan walks readers through TikTok basics and then discusses concerns related to surface level data, privacy breaches, and global security.
Surface Level Issues
To begin with, many users of TikTok post content regarding their daily lives and activities—these are surface level issues. This can be said for other social media platforms, such as Twitter, Facebook, and YouTube. However, this platform promotes personal creativity, and, as mentioned previously, it has a substantially large adolescent audience. That does not mean adults haven’t gotten into the “swing” of things. Take this Tiktok post from @tdobbs1990. He may be spinning to Blanco Brown’s “The Git Up,” but he is also revealing personally identifiable information (PII).

At first glance, users may be participating in a viral video trend. However, if you dig deeper and dissect the video, you may locate hidden identifiers, such as a company uniform or house number. You might even locate the make and model of someone’s car from a video of them singing while driving. For some users, these identifiers may even be hidden in plain sight, like @tdobbs1990, whose full license plate number can be identified in the background of his gas station stage.
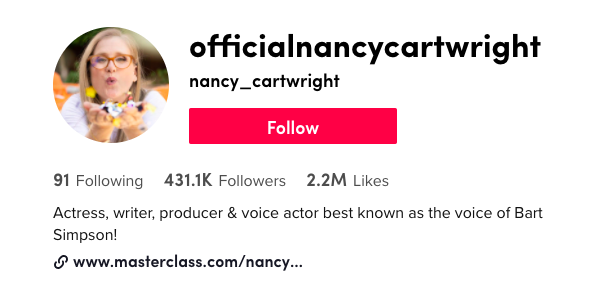
Often, PII can be located in the biography section of the profile, including age, city of residence, educational or professional information, and links to affiliated social media profiles. When summed together, these data points create a detailed profile of the user, formulating endless scenarios that can be beneficial to research and investigations. Below is the bio for Nancy Cartwright, identifying her professional information (the voice of Bart Simpson!) and provides a link to her Masterclass landing page.
Hg’s Word to the Wise
Since its 2016 creation, TikTok has left a rather substantial footprint on modern day social networking. The clout-chasing teenager likely considers this a positive. Viewed through an analytical, research-focused lens, it could be potentially dangerous. With your TikTok account, be wary of the content you post and data you share. If you are planning to use it as an open source intelligence (OSINT) tool, remember the tips mentioned in this blog series and always dissect the videos for hidden bits of intelligence. If you use TikTok only to watch cute puppies and dance along to viral video trends, then cheers to you.
Hg’s Pro OSINT Tip of the Week: Tinfoleak.com
 A seemingly harmless email or website URL could be one click away from disaster. VirusTotal is a free source to combat these cyber scams. Searches by file, URL, IP address, and domain may be performed through the website. VirusTotal will then run searches against 70 antivirus scanners and URL/domain blacklisting services (Malware Domain Blocklist and Threat Hive) to locate any potential threats. Should a URL be safe, it will be marked as Clean; if not, it’ll be marked Malicious. Once collected, the site aggregates and shares any malicious findings through its VirusTotal Community, helping to make the cyber community a safer place to explore.
A seemingly harmless email or website URL could be one click away from disaster. VirusTotal is a free source to combat these cyber scams. Searches by file, URL, IP address, and domain may be performed through the website. VirusTotal will then run searches against 70 antivirus scanners and URL/domain blacklisting services (Malware Domain Blocklist and Threat Hive) to locate any potential threats. Should a URL be safe, it will be marked as Clean; if not, it’ll be marked Malicious. Once collected, the site aggregates and shares any malicious findings through its VirusTotal Community, helping to make the cyber community a safer place to explore.

Are you an analyst or investigator looking for advanced OSINT training on risk assessment and risk monitoring? If so, check out Hg’s webinar series on social media investigative training, where you can attend live sessions and receive CEUs or watch previously recorded sessions to beef up your investigative skills.
 Are you concerned about your company’s or employees’ points of vulnerability through online and open sources? Our skilled analysts are experts at removing personal information that puts you, your business partners, and your family at risk. Learn how our team can assist you in assessing and monitoring your risks.
Are you concerned about your company’s or employees’ points of vulnerability through online and open sources? Our skilled analysts are experts at removing personal information that puts you, your business partners, and your family at risk. Learn how our team can assist you in assessing and monitoring your risks.

Trevor Morgan is an investigative analyst at Hetherington Group, where he uses his open source research skills to extract data from social media accounts, conduct risk assessments, and monitor subjects for clients in pharma, tech, retail, and entertainment. He is a contributing writer to Hg’s Data2Know, Industry Undercover, and OSINT Slack channels. On his lunch break, he can be found outside playing frisbee with his four-legged colleagues.



