This is the second blog post in a three-part series on how social media bots steal brand and personal identities and how you, the investigator, can get them back.
Last week we provided you with the hows and whys of the multi-million dollar industry that legally and illegally generates social media bots. This week we share Hg’s tips on tracking down fabricated accounts and reclaiming a stolen identity.
What is the real impact of social media bots and how do they work?
We know that Amplification Bots are programmed to follow, retweet, and like tweets sent by clients who have bought their services. For example, for $19, I can purchase 5,000 views on my YouTube channel from BuyViews; Devumi has several similar offerings.
If I want more people to go to Hetherington Group’s website, I would create an exciting new YouTube video and attempt to push it out with my small following of colleagues, friends, plus a few of my clients, and my mother. But if I want to significantly hike those numbers—and do so very quickly—I could spend less than $40 with Buyviews and Devumi. The Amplification Bots (a/k/a stolen or fabricated Twitter and YouTube fans) from these companies will like my video and repost it, which will then skyrocket my YouTube video viewing numbers.
The Stealing of Teenagers’ Identities
The smartest bots are based on real people to establish profile credibility. Bots will take a real account, such as @julieblahblah, steal her profile photo, generate a new name for her, or use her real name with a swapped-out character, such as the number 1 for the lowercase l in the nickname (i.e., ju1ie for julie ). If she searched for a pretend account on herself by her name, it wouldn’t appear, since it’s technically different, but looks like the real deal.
photo, generate a new name for her, or use her real name with a swapped-out character, such as the number 1 for the lowercase l in the nickname (i.e., ju1ie for julie ). If she searched for a pretend account on herself by her name, it wouldn’t appear, since it’s technically different, but looks like the real deal.
In a 2018 in-depth investigation, the New York Times detailed how Devumi stole 17-year-old Jessica Rychly’s social identity, along with her profile picture, and recreated it for resale. Her bot account, that to the untrained eye looked like Ms. Rychly’s account, was retweeting graphic pornography. Legally, her photo is personal identifying information, so her identity was stolen, and a law was broken. Ms. Rychly isn’t alone.
“The accounts that most resemble real people, like Ms. Rychly, reveal a kind of large-scale social identity theft. At least 55,000 of the accounts use the names, profile pictures, hometowns and other personal details of real Twitter users, including minors, according to a Times data analysis.” New York Times
The buying and selling of genuine people’s faces, names, and users—as in your kids’ accounts—are for sale minute by minute for pennies and not just by Devumi.
EPICnpc is in the business of buying and selling names on a variety of social media platforms. As an investigator, it’s important to note that if there is no actual personal identifying information being sold, such as in the case of Rychly’s photo being used with a bot twitter account, no real theft of brand or personal identity has occurred.
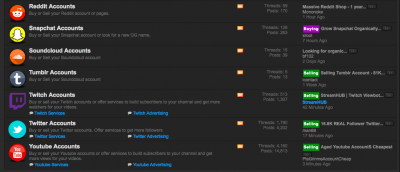
Tracking Down Bot Accounts
What an investigator will do with a bot account depends on the kind of case she has.
Let’s take identity theft as an example: A client calls you, believing his online user name (i.e., handle) has been stolen and is being used to promote products, services, or protests without his consent. You can search the handle using Namechk, pipl, and Google. First get a list of the social media platforms your client has signed up to use as well as his handles, realizing that he may use different ones for different platforms (e.g., @joe_doe; @joeEdoe), then research whether the handle(s) appear on platforms your client didn’t sign up for.
For example, I created and use twitter.com/hetheringtongrp but not instagram.com/hetheringtongrp.
If this Instagram account were using my name to promote products I don’t endorse, opinions I don’t have, or illegal practices, I could write Instagram and ask to have the fraudulent account removed. Please note, however, the social media platform will need to prove someone else is using your handle. In other words, does Hetherington Group own the right to that name, or is it commonly used, untrademarked, or with no established first usage? If so, this could become a social media squatting law suit and get quite complicated legally or expensive to purchase from the original owner.
For the record, this happens all the time. It’s especially noticeable on Facebook, which allows you to Report An Imposter account by finding and selecting the Report button on its page.
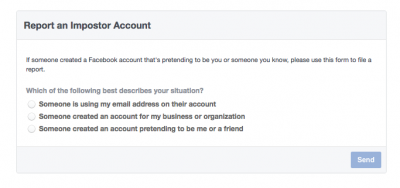
If you don’t have an account on these social media sites, there are still ways to fix things. Use the following URLs to make a report. Follow this links for each of the social media platforms contact page: Facebook, Instagram, Twitter.
Once you report an impersonated, stolen, or hacked social media account, you’ll often find yourself waiting and will, perhaps, need to re-report the issue multiple times before getting a response. No law enforcement agency is going to help. There’s no company phone number to call, and no customer service rep to help (or care). It takes persistence and vigilance: Two qualities every good investigator has!
Follow us on Twitter @HetheringtonGrp to catch next week’s post on investigating stolen images!
Like what you’re reading? Become an Hg member and learn how to maximize your online investigations with shortcuts, tips, tricks, better investigative tools, and advanced research techniques for all skill levels. As an added benefit, subscribers get access to our Opt Out Index containing over 200 active links to assist you in getting your private data off the Internet. From Abika to ZoomInfo, we’ve got you covered!



