 By Cynthia Hetherington
By Cynthia Hetherington
This past year I had the privilege to address The Canadian Institute of Chartered Business Valuators on the topic of online and cyber investigation applications. CBV is intensely interested in work efficiency, excellent content, and the resources that can support those endeavors. Our session was a great success and was included in the CBV Journal of Business Valuation 2020 Edition. The following is an excerpt of the session and article, in hopes of providing beneficial knowledge to information professionals, accountants, researchers and those cyber-curious truth seekers who, like CBV, value efficiency in their productivity.
This is an excerpt from Hg’s FactSheet, Online Intelligence Tips for Forensic Accounting Investigations. You can download the full report here.
Today in Forensic Accounting
In today’s data-intense, digital world we’ve all gone cyber in our endless quest for answers. Everything in the forensic accounting world, business valuations, and accounting involves data collection and fact checking. We are all invested in analyzing large datasets, finding anomalies, and extracting key information and insights.
Despite the variety of cybertools at our disposal—from optical characterization and recognition software to AI technology—an entirely different set of digital tools is proving especially useful to forensic accountants in tracking down and tracing the actions of people. The easiest to access and most readily available are open source, social media sites, search engines, and databases—some free, some not. That said, fee-based tools can hasten the investigative process, making it even more intelligent.
Following the resource tips described in this blog series will allow you to gather critical intelligence on people, historical topics, or events through public and not-so-public records without resorting to subterfuge or subverting security protocols. Understanding how these searches work—the data infrastructure or physical architecture of how information is disseminated, collected, captured, and stored—is crucial if obliged to explain your methodology to a client or testify as an expert witness in court. If uncertain about the authenticity of the information you’ve gleaned from open sources such as Facebook or Twitter, it is important that you state that clearly in a report, particularly if it serves as the basis for your analysis.
When all else fails …
What if you’ve hit a wall, even though you’re convinced the proof you’re after is out there? You can track down information on social media searches in a faster, less roundabout way by using keywords. Facebook, for example, no longer permits cell and email searches. You know, however, that information tends to be exchanged more readily on this platform, so monitoring the chatter is important to your investigation.
Google searches for Facebook
Using Google to search for Facebook content can lead you to the proof you think is out there waiting to be discovered. Enter the following: site:facebook.com “cellphone number” or “email address,” “business partner address” or any other keyword or words relevant to your search. Make sure you enclose them in quotation marks, then watch as a slew of results pop up.

Proximity searches
Another trick you can use to narrow your Google search and turn up quicker matches is to conduct what’s known as a proximity search. By inserting an asterisk between two expressions or keywords, in this case the name of your subject and a likely connection—“john doe” * “jane doe”—you can link the two to uncover still more connections. Anything on one side of the asterisk must be within 15 words of the other side.
Say your audit reveals that John Doe, the procurement officer for a major bank, has been engaged in illicit business dealings with Jane Doe, a person of interest. Do a proximity search by pairing each of their names in any number of different ways, such as in combination with a cellphone number, a business address belonging to individuals or agencies connected with the bank, or business associations in common.
Google.com/alerts
Once you’ve exhausted every conceivable combination you can think of that might link the two suspects, go to Google.com/alerts, as shown in this screen grab. Start your search again, using asterisks, the same keywords and email addresses as before, but opt to see “all” results, not just “best” results.
Archive.org
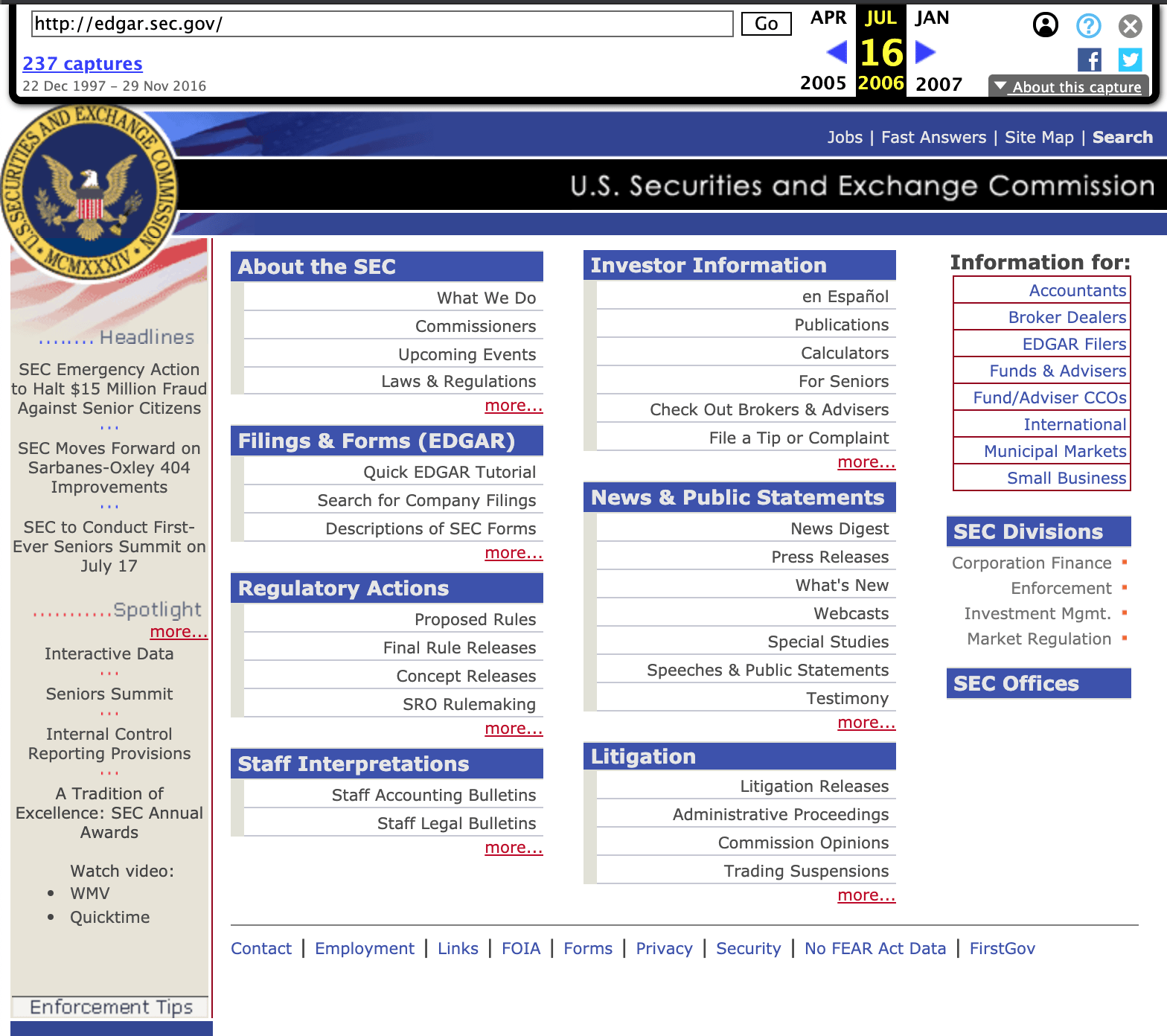
To bolster your casework, you may need to comb through digital content dating back 20+ years. Archive.org is not only free but among the most reliable global databases available. Its homepage boasts having archived more than 538 billion web pages. A visit can prove particularly helpful when working on intellectual property cases.
Enter the website of interest, and Archive.org will indicate how far back its archived pages extend. Here, we have entered EDGAR, the SEC’s database. On the top banner timeline, you learn that Archive.org has 237 captures between December 22, 1997 and November 29, 2016. As shown here, this is what appeared on the web page on June 16, 2006.
If you need to roll the clock back even further, newspaper and journalistic databases are an amazing resource. They capture content globally, nationally and locally in multiple languages, reaching back to at least the 1970s, if not earlier.
Final thoughts
Thorough research is necessary in any type of investigation and requires knowledge of available sources and services to accurately answer the questions asked. Whether you are a forensic accountant, due diligence analyst, special agent, or private investigator, it is necessary to implement a consistent methodology that allows you to approach your research in a systematic way, record your findings, and report your analysis.
In asset investigation or debt recovery work, establish a clear starting point for your attack. Document everything you find—even the smallest details. Save all your files. A random mention of flying lessons on a social media page may, a few months later, prompt you to search for aircraft tail numbers. Pair your excellent searcher skills with some of the professional tools and hack tricks of the trade to fill out your report.
The quest to uncover fraud in its many guises is a never-ending one. At least once armed with the cybertools discussed in this series, you have more of a fighting chance to outsmart the canniest of them.

Hg OSINT TRAINING OPPORTUNITY: Online Social Media Primer, 300 minutes 5 CEUs
LIVE Webinars: August 2 @ 2:00 pm – August 30 @ 3:00 pm EDT
How well are you incorporating social media into your cyber investigations? No worries—we all start somewhere! This online social media primer details the treasure trove of riches social media offers to an open source investigator. With just a few mouse clicks away, leads can be discovered, facts challenged, and game changing details can be unveiled—all in support of a case!
This introductory primer series will teach you why to use these platforms, how to crack them, where to look, what nuances and leads you need to chase down, and how they are all interrelated. We’ll also discuss how to capture content per service, so you can present it in your reports. Each webinar covers a single social media platform and its specific details. Platforms to be covered include Facebook, LinkedIn, Twitter, Instagram, and Reddit.
 RISK ASSESSMENT
RISK ASSESSMENT
Are you concerned about your company’s or employees’ points of vulnerability through online and open sources? Our skilled analysts are experts at removing personal information that puts you, your business partners, and your family at risk. Learn how our team can assist you in assessing and monitoring your risks.
 Cynthia Hetherington, MLS, MSM, CFE, CII is the founder and president of Hetherington Group, a consulting, publishing, and training firm that leads in due diligence, corporate intelligence, and cyber investigations by keeping pace with the latest security threats and assessments. She has authored three books on how to conduct investigations, is the publisher of the newsletter, Data2know: Internet and Online Intelligence, and annually trains thousands of investigators, security professionals, attorneys, accountants, auditors, military intelligence professionals, and federal, state, and local agencies on best practices in the public and private sectors.
Cynthia Hetherington, MLS, MSM, CFE, CII is the founder and president of Hetherington Group, a consulting, publishing, and training firm that leads in due diligence, corporate intelligence, and cyber investigations by keeping pace with the latest security threats and assessments. She has authored three books on how to conduct investigations, is the publisher of the newsletter, Data2know: Internet and Online Intelligence, and annually trains thousands of investigators, security professionals, attorneys, accountants, auditors, military intelligence professionals, and federal, state, and local agencies on best practices in the public and private sectors.



